Deploying Deep freeze with K2000 Post install tasks
Has anyone else worked with deep freeze or had success deploying it with post install tasks? I have been trying to come up with a plan for deployment and was hoping to do the following:
- Install via post task in the unthawed state
- Freeze as my last task
Any best practices when deploying with the K2000? Is this something I should just deploy always at the end of the post install tasks?
0 Comments
[ + ] Show comments
Answers (2)
Please log in to answer
Posted by:
SMal.tmcc
8 years ago
Piece of cake, been doing this for years. Even helped them with info for this KKE on that
http://stage.kace.com/mx/support/training/kke/archive?id=37AC3F66-AD51-4F8D-8372-EBA9ED5AA59F
The secret is to set a command line password when you compile your DF installs.
These are for x64 calls, for x86 use c:\windows\system32\...
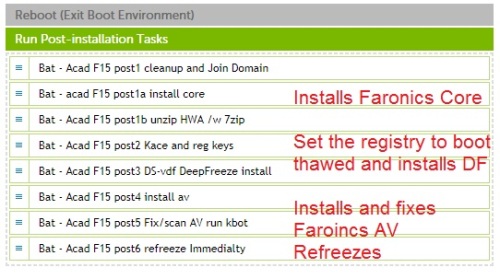
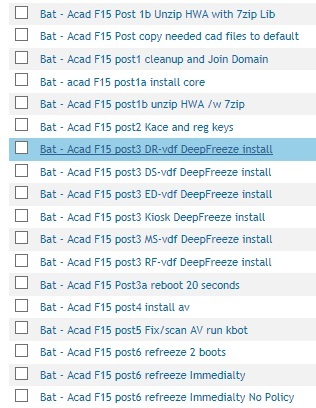
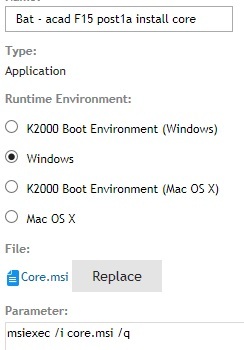
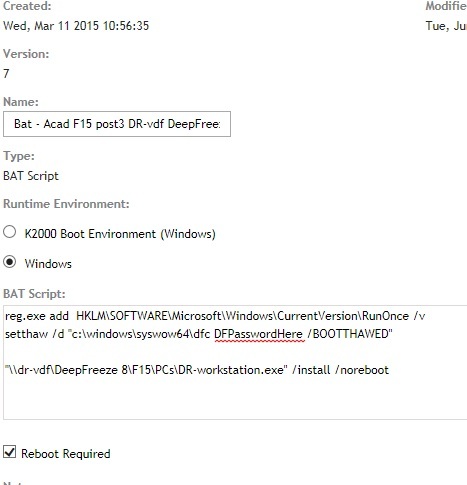
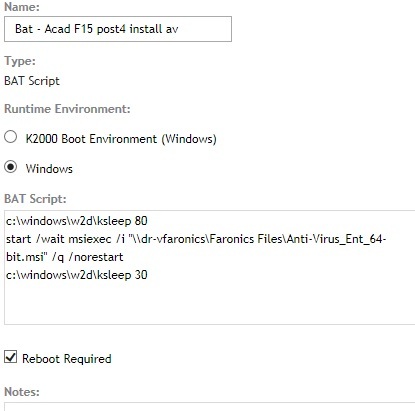
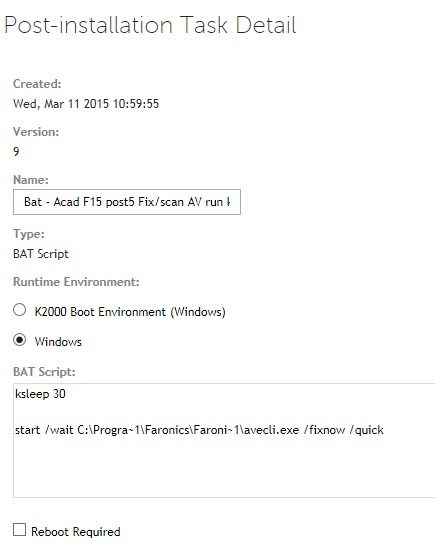
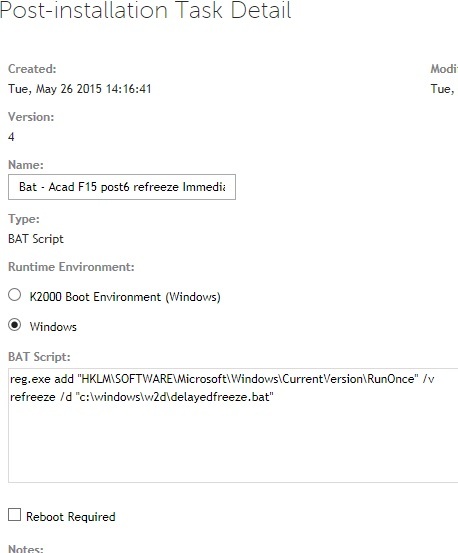
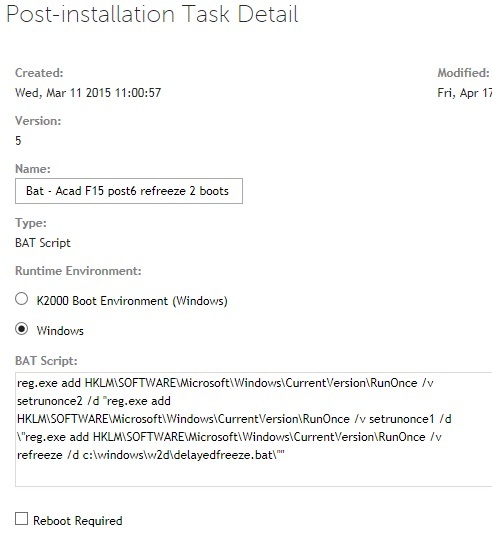
http://stage.kace.com/mx/support/training/kke/archive?id=37AC3F66-AD51-4F8D-8372-EBA9ED5AA59F
The secret is to set a command line password when you compile your DF installs.
These are for x64 calls, for x86 use c:\windows\system32\...








Comments:
-
Holy Moly. This looks to be perfect.
What are you using in your delayedfreeze.bat?
I had no clue Faronics Core existed. Trying to get that setup now. I am just getting the lay of the land again with Deep Freeze. Its been about 5 or 6 years since I have touched it. - joemalone 8 years ago-
I use a local file to call a protected file on a server that only certain users can see. That way when we change the DF command line password all we need to do is modify it on the server. I also use the k1000 scripting to freeze, thaw, autologin and stop autologin - SMal.tmcc 8 years ago
-
And you've had better luck with the K1000 handling the thawing and freezing than using the Deep Freeze console? We are wrestling with this now, and our K1000 scripts work, but not all the time. Unfortunately, we are running a very old version of deep freeze. - jamie1069 8 years ago
-
It just saves needing to open the console and kace to deploy tasks, This just makes it a one stop tech tool - SMal.tmcc 8 years ago
-
get to the newest version. the core is handy is you are also using their AV. They also now have a web version but we are sticking with DF servers. Post 3 I have a different install to point the DF install to the server for that site. - SMal.tmcc 8 years ago
-
Got Core setup and running. Is there a specific way to be able to manage deep freeze from it. I am not finding much if any documentation but I read you are supposed to be able to. - joemalone 8 years ago
-
nvm I think I found the right document! http://www.faronics.com/assets/YDF_Manual.pdf - joemalone 8 years ago
-
feel free to email if you need more detailed help. - SMal.tmcc 8 years ago
-
If you're using the latest version of Deep Freeze, they added a new install switch (/thawed) to allow the install to remain thawed.
Small change, only saves you a step, but still helpful.
DFSetup.exe /Install /thawed /NOREBOOT - animerunt 8 years ago
Posted by:
SMal.tmcc
8 years ago
sorry about missing that part I have a local batch file that calls a batch on a server share that only our installer user has access to so even if users find the local bat they cannot see it due to rights.
ksleep 20
call \\dr-acad\programs\installs\w2d\frozenpolicy.bat
reg.exe ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v legalnoticecaption /d "TMCC Academic Use Statement" /f
reg.exe ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v legalnoticetext /d "TMCC Computer Use Policy - TMCC General Access Computer Labs are educational computer facilities open to all students, faculty and staff at TMCC. If not enrolled or employed at TMCC, then access is not allowed. Identification may be requested. Lab Assistants may monitor computer use. Students needing a computer to do their homework will have preference over students that are playing games or participating in Internet chat. Students who are on the chat lines or playing games are welcome, but will be advised to come back when the labs are not busy. Viewing or printing pornographic material that can be viewed by others is not allowed in any of the Labs or Kiosks. Cell-phone use in the labs is prohibited. Emergency calls can be received, but the user must step outside of the Lab to continue the conversation. Absolutely no food or beverages are allowed in the labs! Maintain a friendly and quiet lab for other students to do their work. Maintain a quiet work area: Loud boisterous behaviour is not acceptable; the Lab is not a place to socialize, as it's distracting to others. Children are not to be left unattended in the labs. Head count and surveys: In order to effectively use technology resources, head counts or surveys will be taken by the lab monitor. Please provide them with your cooperation. Closing time: The labs must close promptly at the scheduled time. Your cooperation in abiding with the closing time would be greatly appreciated. ACTIVITIES IN VIOLATION OF TMCC'S COMPUTER USE POLICY - Unauthorized use of a computer account. Using the campus network to gain unauthorized access to any computer systems. Connecting unauthorized equipment to the campus network. Using electronic mail to harass or threaten others. This includes, but is not limited to, sending repeated, unwanted Email to another user. Transmitting or reproducing materials that are slanderous or defamatory in nature or that otherwise violate existing laws, NSHE, or College regulations. Displaying obscene, lewd, or sexually harassing images or text in a public computer, facility, or location that can be in view of others. Initiating or propagating electronic chain letters inappropriate mass mailing. This includes, but is not limited to, multiple mailings to the TMCC Campus, newsgroups, mailing lists, or individuals forging the identity of a user or machine in an electronic communication. Attempting to monitor or tamper with another user's electronic communications, or reading, copying, changing, or deleting another user's files or software without the explicit agreement of the owner. Unauthorized attempts to circumvent data protection schemes or uncover security loopholes. This includes creating and/or running programs that are designed to identify security loopholes and/or decrypt intentionally secure data. Knowingly or carelessly performing an act that will interfere with the normal operation of computers, terminals, peripherals, or networks. This includes tampering with or removing computer hardware or software. Knowingly or carelessly running or installing on any computer system or network, or giving to another user a program intended to damage or to place excessive load on a computer system or network. This includes, but is not limited to, programs known as computer viruses, Trojan horses, and worms. Deliberately wasting/overloading computing resources, such as printing excessive copies of a document. Violating terms of applicable software licensing agreements or copyright laws. Violating the TMCC Copyright Infringement policy, copyright laws and their fair use provisions through inappropriate reproduction or dissemination of copyrighted text, images, etc. Using college resources for commercial activity such as creating products or services for sale." /f
reg.exe add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\WinLogon" /v AutoAdminLogon /d 0 /f
reg.exe delete "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\WinLogon" /v defaultpassword /f
if EXIST c:\windows\SysWOW64\dfc.exe (c:\windows\SysWOW64\dfc.exe DFPassword /FREEZENEXTBOOT) ELSE (c:\windows\System32\dfc.exe DFPassword /FREEZENEXTBOOT)
start /wait shutdown -r -t 15 -f
Comments:
-
we would have used kace scripting but I found a length limit bug for scripts to about 800 characters so the reg add for the policy would fail - SMal.tmcc 8 years ago


