
Specops Deploy 3.0
by Bob Kelly
There are a large number of organizations making use of Group Policy for software deployment. It has many benefits, but also many weaknesses: it cannot handle legacy/command-line installations, its reporting capabilities are nil, it cannot be scheduled, it does not handle slow links well and it cannot perform installations once a user has already logged onto the workstation. Specops Deploy aims to expand Group Policy in order to provide these and other missing features- features you can attain without the need to abandon Group Policy for software deployment.
The option to expand upon Group Policy instead of replacing it is the real beauty of Specops Deploy- for most organizations (unless you are starting up a fresh new network or are overhauling your existing one) biting of on a replacement system for application deployment can be a hard sell. With so many relying on (or just trying to get by with) Group Policy for application deployment, Specops Deploy presents a solution that does not require changing the way you do business while resolving most all the issues that make managing software deployment with Group Policy so frustrating.
First we will cover the installation of Specops Deploy, followed by a review of the two key capabilities likely to attract you to Specops Deploy: its deployment options and reporting capabilities. Finally, we will discuss how Specops handles distribution with its BITS support. As usual we'll close with some closing comments, so let's get started!
Installation
A very intuitive setup assistant is provided to ensure you have all the requirements necessary as well as to help you with the actual server and client installation of Specops Deploy itself.
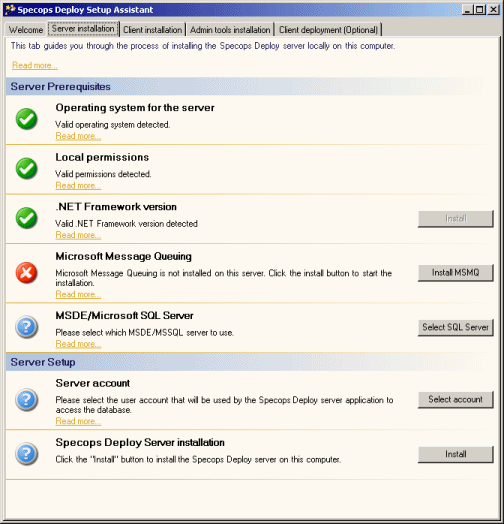 As you can see from the screen shot of the Specops Deploy Setup Assistant, my server was missing MSMQ. I did need my Server Installation CD to complete the installation, but pressing the “Install MSMQ” button completely automated the installation of this prerequisite. For a database, you can use the included MSDE or SQL Server, for SQL Server 2000 SP3 or later is required (I needed to install SP3).
As you can see from the screen shot of the Specops Deploy Setup Assistant, my server was missing MSMQ. I did need my Server Installation CD to complete the installation, but pressing the “Install MSMQ” button completely automated the installation of this prerequisite. For a database, you can use the included MSDE or SQL Server, for SQL Server 2000 SP3 or later is required (I needed to install SP3).
The client installation actually walks you through creating a GPO for the Microsoft .NET Framework and the Specops Deploy GPO Extension and assigning it to target systems. Because Specops Deploy uses Group Policy natively, the Specops Deploy GPO Extension is simply a single dll which is only loaded when in use. Instructions are actually carried out by Group Policy using this extension to provide its enhanced capabilities.
Installation of the Admin Tools (The Specops Deploy Control Center) requires Windows XP or later, so I was unable to install it on my server which was a Windows 2000 server. However, the Control Center can be run from anywhere on the network; installing this on another system was quick and easy.
Overall installation was surprisingly simple considering the actual complexity of getting the prerequisites installed and client extensions deployed. The installation of the server and my test clients (even with my fumbling for CDs) took only about a half an hour.
Deployment Options
Specops Deploy provides a strikingly simple interface, broken out into Packages, Targets, and Deployments. In addition there is also a "Deploy Package Wizard" that takes you through the process of creating a package, target and deployment step-by-step.
When specifying the location of a package it is recommended that you include only the package and required source files the chosen folder. This is because Specops Deploy distributes not just the specified file, but the folder for the specified file (including any other files and subfolders present alongside it). For MSI packages, you'll probably want to store your MSI in its own folder (with no subfolders) but for legacy setups you are deploying as command line installations, a folder and its subfolders may well be what you need to get the job done.
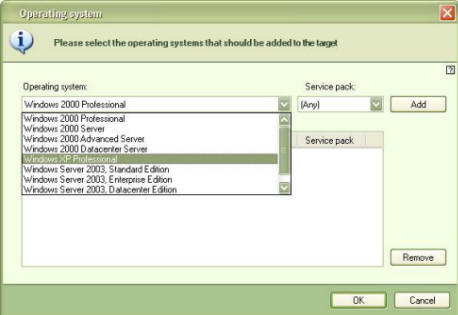 Groups of targets are created in the “Targets” view of the Specops Deploy Control Center. By default, you have “All computers” and “All users” and may create others by simply pressing the “New Target” button. When you do so, you are first asked to specify if this is a Computer target or a User target, then you choose a name for the target group and select the target criteria. This is another place where you have the opportunity to move beyond the traditional limits of group policy- you may choose Security Groups, Computers, Organizational Units, Sites or Operating Systems. Multiple qualifiers may be specified, and for operating systems, you have the choice of specifying the edition of Windows as well as the service pack number (see screen shot). You may even specify certain criteria for systems to be excluded from the target group.
Groups of targets are created in the “Targets” view of the Specops Deploy Control Center. By default, you have “All computers” and “All users” and may create others by simply pressing the “New Target” button. When you do so, you are first asked to specify if this is a Computer target or a User target, then you choose a name for the target group and select the target criteria. This is another place where you have the opportunity to move beyond the traditional limits of group policy- you may choose Security Groups, Computers, Organizational Units, Sites or Operating Systems. Multiple qualifiers may be specified, and for operating systems, you have the choice of specifying the edition of Windows as well as the service pack number (see screen shot). You may even specify certain criteria for systems to be excluded from the target group.
With Group Policy alone you have to trigger a reboot for a computer assigned installation (or removal) to take place, but not here! After successfully deploying a package to a few test machines, I instructed Specops Deploy to “Undeploy” the package and I did not restart the clients. Sure enough, in about two hours, the package removed itself from the specified targets. Why two hours? Installations take as long to trigger as any other Group Policy update would. By default this is 90 minutes, plus a random interval between 0 and 30 minutes. However, you can force an update using GPUPDATE.EXE (or “SECEDIT /Refreshpolicy machine_policy” on Windows 2000) and Specops Deploy will see the deployment and take action right away.
As with any Group Policy deployment you can immediately view the results in the Windows Application Event Log, but it is the remote real-time deployment status that really makes Specops Deploy shine.
Deployment Feedback
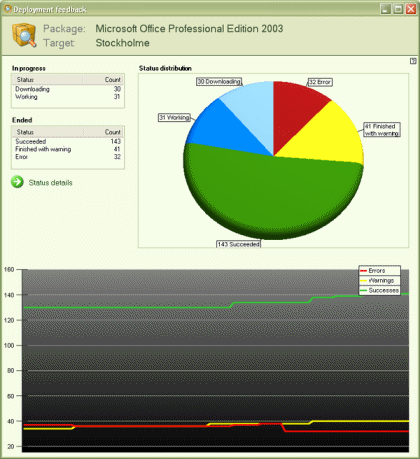 One of the most frustrating things about Group Policy deployment has got to be a lack of reporting. Warning: to go from no reporting at all to the rich reporting provided by Specops could cause shock to some administrators!
One of the most frustrating things about Group Policy deployment has got to be a lack of reporting. Warning: to go from no reporting at all to the rich reporting provided by Specops could cause shock to some administrators!
The report is very functional and easy to read. You see "in progress" and "ended" deployments in two simple tables that provide counters for the current status. Alongside this: a pie chart, and below: a line graph that constantly updates. In fact all of these update whenever the deployment feedback view being displayed. This instant feedback provides more granular detail when you select a status from either table and press the "Status details" link. From here a new window is presented with details for systems reporting the selected status. For example, selecting Error and pressing "Status Details" shows you a breakdown of whatever errors were returned (such as by internal Windows Installer error) complete with error text.
Package Deployment Process
I mentioned before that Specops Deploy “downloaded” the packages prior to installation. I know it raised a flag in my head when I heard it: is the source kept local after the installation is complete? What about MSI installation source pointers? Worry not; the guys at Special Operations Software have it covered.
BITS 2.0 is used to download the installation locally. This is the same "trickle" download feature used by Windows Update and Software Update Services (SUS). In this way, the download uses SMB and is not restricted to HTTP so you do not have to install a web server and will have no problem installing from any location (such as from DFS or any file share). If BITS 2.0 is not found on a target computer, it will automatically revert to an SMB connection for the download. Once the file is downloaded, the installation takes place from this downloaded copy of the installation files.
 As discussed earlier, the entire folder contents (as well as any subfolders and their contents) are copied to target systems for the installation and are then removed. So you are covered if you are dealing with a legacy setup that requires multiple files (or directories of files). If the package is a Windows Installer setup, the source location is pointed back to the original path on your network in case the package needs to be repaired or any features are set to install on demand.
As discussed earlier, the entire folder contents (as well as any subfolders and their contents) are copied to target systems for the installation and are then removed. So you are covered if you are dealing with a legacy setup that requires multiple files (or directories of files). If the package is a Windows Installer setup, the source location is pointed back to the original path on your network in case the package needs to be repaired or any features are set to install on demand.
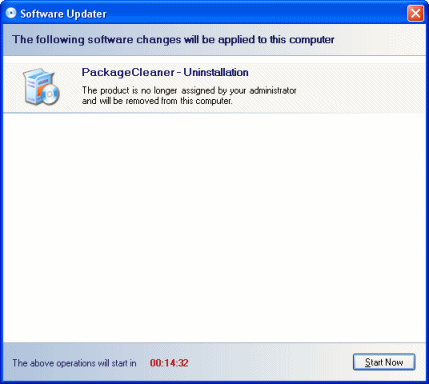
 During installation, a taskbar icon appears to indicate status- click on it and get more details as to what is going on (see screen shot).
During installation, a taskbar icon appears to indicate status- click on it and get more details as to what is going on (see screen shot).
When creating a deployment in the Specops Deploy console, you can choose a custom message to display to users but there are currently no options to allow users to abort an installation or delay its installation. The timer starts at fifteen minutes and may be initiated sooner by the user if they hit the provided "Start Now" button.
Finally, when you create a deployment you can also specify if the installation should take place as soon as possible (default) or not before a specified date and time. This is also where you may dictate if the installation should take place only during startup, only after the computer has been started (or logged on), or either.
Closing Comments
| Specops Deploy logs pertinent information to the Application log in the Windows event log. However, if you want a more, you may turn on a verbose trace log by setting the following value in the registry: SubKey: HKLM\Software\SpecopsSoft\ Specops Deploy\Client Side Extension\ Debug Value: 1 If you do so, the log file will be updated here: %WINDIR%\Debug\UserMode \SpecOpsGpProcessor.log. However, the information that really matters can be found right in your application event log, so there should never be reason to turn this on. |
The simple interface and robust reporting will be appealing to everyone, but one of the biggest benefits to administrators has got to be its support for legacy setup packages. Even with more and more vendors moving to Windows Installer setups, it is still annoying to find that some of these Windows Installer setups to not lend themselves to deployment via Group Policy. There has always been the argument that using a vendor supported command line installation is preferable to repackaging setups. But no matter what side of the fence you are on when it comes to this mindset, few will argue that the option to deploy a setup using its command line support is sometimes necessary. Many create MSI wrappers (Microsoft even provides such wrappers for the latest Windows service packs) in order to deploy command line installations via Group Policy. Specops Deploy eliminates this need for added complexity by allowing you to simply specify the command line installation parameters in your deployment package.
The interface can take just a little getting used to when creating deployments and packages. The "Deploy Package Wizard" is a standard wizard interface with a “next” button to advance to the next step. However, actions like creating a new package, deployment or target may be spread across more than one page of options. As these pages have a standard “OK” and “Cancel” at the bottom (and not a "Next" button to proceed to other views) so to move between the options available, you use a simple navigation pane displayed at the left of the screen. The first couple of times you use it you are likely to complete only the first screen and press OK (or hit "Enter") and will need to hit "edit" to get back in and update any other options you wish.
Overall, Specops Deploy is a very impressive offering that takes Group Policy and makes it a whole lot better. The things you tolerate as a result of your decision to employ Group Policy for software deployment can be attained without abandoning Group Policy. Pricing starts at $1900 USD for 100 workstations or servers (including 12 months maintenance) and the folks at Special Operation Software are confident enough in their product to offer a 20 day fully functional trial version of Specops Deploy.
3/16/05
Bob Kelly
AppDeploySM

Comments