The Following is a Security Overview and Analysys of UltraVnc 1.0.9.6.2 This has been verfied and tested by me.
|
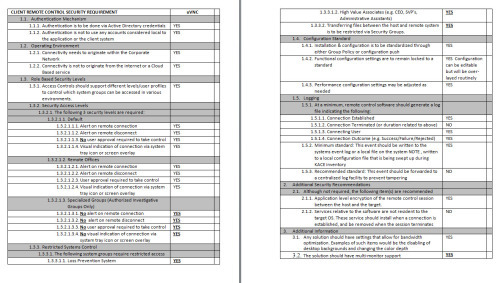
CLIENT REMOTE CONTROL SECURITY REQUIREMENT |
uVNC |
|
|
1.1. Authentication Mechanism
|
|
|
|
1.1.1. Authentication is to be done via Active Directory credentials |
YES |
|
|
1.1.2. Authentication is not to use any accounts considered local to the application or the client system |
YES |
|
|
1.2. Operating Environment |
|
|
|
1.2.1. Connectivity needs to originate within the Corporate Network |
YES |
|
|
1.2.2. Connectivity is not to originate from the internet or a Cloud Based service |
YES |
|
|
1.3. Role Based Security Levels |
|
|
|
1.3.1. Access Controls should support different levels/user profiles to control which system groups can be accessed in various environments. |
YES |
|
|
1.3.2. Security Access Levels
|
|
|
|
1.3.2.1. The following 3 security levels are required: |
|
|
|
1.3.2.1.1. Default |
|
|
|
1.3.2.1.1.1. Alert on remote connection |
YES |
|
|
1.3.2.1.1.2. Alert on remote disconnect |
YES |
|
|
1.3.2.1.1.3. No user approval required to take control |
YES |
|
|
1.3.2.1.1.4. Visual indication of connection via system tray icon or screen overlay |
YES |
|
|
1.3.2.1.2. Remote Offices |
|
|
|
1.3.2.1.2.1. Alert on remote connection |
YES |
|
|
1.3.2.1.2.2. Alert on remote disconnect |
YES |
|
|
1.3.2.1.2.3. User approval required to take control |
YES |
|
|
1.3.2.1.2.4. Visual indication of connection via system tray icon or screen overlay |
YES |
|
|
1.3.2.1.3. Specialized Groups (Authorized Investigative Groups Only) |
|
|
|
1.3.2.1.3.1. No alert on remote connection |
YES |
|
|
1.3.2.1.3.2. No alert on remote disconnect |
YES |
|
|
1.3.2.1.3.3. No user approval required to take control |
YES |
|
|
1.3.2.1.3.4. No visual indication of connection via system tray icon or screen overlay |
YES |
|
|
1.3.3. Restricted Systems Control
|
|
|
|
1.3.3.1. The following system groups require restricted access |
|
|
|
1.3.3.1.1. Loss Prevention System |
YES |
|
|
1.3.3.1.2. High Value Associates (e.g. CEO, SVP’s, Administrative Assistants) |
YES |
|
|
1.3.3.2. Transferring files between the host and remote system is to be restricted via Security Groups. |
YES |
|
|
1.4. Configuration Standard
|
|
|
|
1.4.1. Installation & configuration is to be standardized through either Group Policy or configuration push |
YES |
|
|
1.4.2. Functional configuration settings are to remain locked to a standard |
YES Configuration can be editable but will be over-layed routinely |
|
|
1.4.3. Performance configuration settings may be adjusted as needed |
YES |
|
|
1.5. Logging
|
|
|
|
1.5.1. At a minimum, remote control software should generate a log file indicating the following: |
|
|
|
1.5.1.1. Connection Established |
YES |
|
|
1.5.1.2. Connection Terminated (or duration related to above) |
YES |
|
|
1.5.1.3. Connecting User |
YES |
|
|
1.5.1.4. Connection Outcome (e.g. Success/Failure/Rejected) |
YES |
|
|
1.5.2. Minimum standard: This event should be written to the systems event log or a local file on the system |
YES, written to a local configuration file that is being swept up during KACE inventory |
|
|
1.5.3. Recommended standard: This event should be forwarded to a centralized log facility to prevent tampering |
NO |
|
|
|
|
|
2.1. Although not required, the following item(s) are recommended |
|
|
|
2.1.1. Application level encryption of the remote control session between the host and the target. |
YES |
|
|
2.1.2. Services relative to the software are not resident to the target OS. These service should install when a connection is established, and be removed when the session terminates |
NO |
|
|
|
|
|
3.1. Any solution should have settings that allow for bandwidth optimization. Examples of such items would be the disabling of desktop backgrounds and changing the color depth |
YES |
|
|
3.2. The solution should have multi-monitor support |
YES |
|

Comments