Here's an example of how you can use powershell to extract more complex values than you can get from just using wmic or registry reads...
Uptime is a simple example. Yes, you can use filters such as Uptime > 4 days in your searches or smart labels, so for practical purposes maybe not wonderful, but it is a simple example.
Since WMI returns uptime as a reference to the last reboot of the system, we need to do something a little bit more complex to get the number of seconds of uptime, like you can get in a *nix based system.
Since all of our systems have Powershell available I decided to leaverage that for our solution.
[int]((get-date)-[system.management.managementdatetimeconverter]::todatetime((get-wmiobject -class win32_operatingsystem).Lastbootuptime)).TotalSeconds
Let's break this down
[int] means we are casting (in other words converting) the result to an integer. By default date/time math will result in floating point results much of the time, and we want a simple integer value instead.
(get-date) returns an object with the current system date and time, on the computer from which it is being run.
[system.management.managementdatetimeconverter]::todatetime references a system assembly for a function to convert system date formats into the general date/time type used by .net (or in this case Powershell.)
(get-wmiobject -class win32_operatingsystem).Lastbootuptime is one way in Powershell that you can retrieve the date/time of the last system startup.
So if you follow the parenthesis, we're subtracting the last boot date/time from the current date/time, which results in a date/time span object, which has properties, one of which is TotalSeconds. We could just as easily return the span as minutes, hours, days, etc.
Running this from powershell returns the uptime in seconds, so to implement this as a Custom Inventory Rule, just use the following.
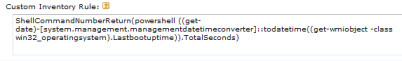
Or to make it a bit easier to implement you can cut and past the following:
ShellCommandNumberReturn(powershell [int]((get-date)-[system.management.managementdatetimeconverter]::todatetime((get-wmiobject -class win32_operatingsystem).Lastbootuptime)).TotalSeconds)
This is just an example of what you can do using the ShellCommand* methods with Powershell. Generally you can decant most expressions into a single line of code returning just what you want which means you can avoid posting script files on shares or using the scripting interfaces, when all you want is to add custom inventory values.

ShellCommandNumberReturn(wmic os get lastbootuptime)
Running from a command prompt:
C:\Users\Jason>wmic os get lastbootuptime
LastBootUpTime
20121101020148.540310-300 - jknox 11 years ago
PS C:\> [int] (New-TimeSpan -Start ([system.management.managementdatetimeconverter]::todatetime((Get-WmiObject -Class Win32_OperatingSystem).LastBootupTime))).TotalSeconds - ncsutmf 11 years ago