Need SQL report that tells me if any process's are running from users appdata directory or sub directories
I am trying to create a k1000 sql report that shows any running process's that contain the word appdata in the commadline path. using WMIC I can run "WMIC PROCESS where (commandline like "%appdata%") get name, commandline" and see where software is running from, would like to turn that into a k1000 report to help us look for malware running in the users directory.
Answers (3)
the table you are looking for is MACHINE_CUSTOM_INVENTORY.
I was looking at this but could not get the wmic command working. The report wizard in 5.4 allows you to select customer inventory field by name (rather than ID number) , makes life a lot easier. I took your command line, created a custom inventory rule (ShellCommandTextReturn) then created a report using the wizard, the custom inventory is a radio button. Only problem I have is the command line, could you check the syntax and let me know?
This would be cool to incorporate scheduled reports by email
Comments:
-
Just realized the table you are looking for first needs to be created. Use a customer inventory rule under software (add new item) with the command. The text return is put in MACHINE_CUSTOM_INVENTORY, you can pull this using SQL or as i mentioned in the new report wizard - Scott Smith 11 years ago
-
that would make a good scheduled report, 95% of the time any malware we find is running in the the users temp dir. - SMal.tmcc 11 years ago
Regarding the report, I dont think there is a way to pull the actual data into the report. However, if you want to build an alerting system based on the detection of malware there are other options. As a side note, I am not claiming that you should use KACE for AV detection, this is simply a Defense in Depth strategy. KACE can be a useful tool for zero day (or dead in the water malware events), where the AV vendor does not have IDE however they know or you know the process that is being launched by the malware.
Back to the task at hand, you could use the custom inventory rule in the above scenario to detect specific processes then build a label to group those systems together (to then create a removal script to deploy to the systems in that label ). You can still run the full wmic process , you will see the results in the computer inventory. (see image)
I am working on a blog post, I think this is very useful stuff. I will continue to work on this.
The SQL for my custom inventory report is below, I built using the 5.4 wizard
SELECT MACHINE.NAME AS SYSTEM_NAME, (SELECT MACHINE_CUSTOM_INVENTORY.STR_FIELD_VALUE FROM MACHINE_CUSTOM_INVENTORY WHERE MACHINE_CUSTOM_INVENTORY.ID=MACHINE.ID AND MACHINE_CUSTOM_INVENTORY.SOFTWARE_ID=1320) AS MACHINE_CUSTOM_INVENTORY_0_1320 FROM MACHINE ORDER BY SYSTEM_NAME, MACHINE_CUSTOM_INVENTORY_0_1320
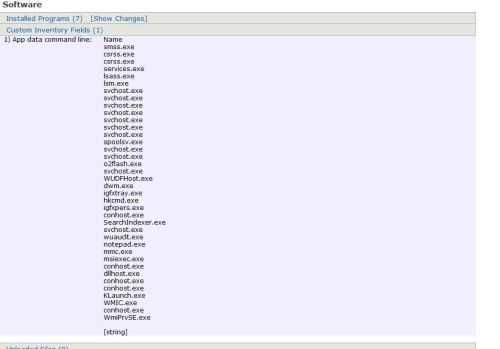
Comments:
-
hey thanks, Just being able to go and look in the software inventory and see the machines running items in an area they should not be is great, Will work on the report I am going to add some exceptions for couple of items. - SMal.tmcc 11 years ago
-
what did you put in for you custom software inventory line? I am getting computer names but no exe's in my report - SMal.tmcc 11 years ago
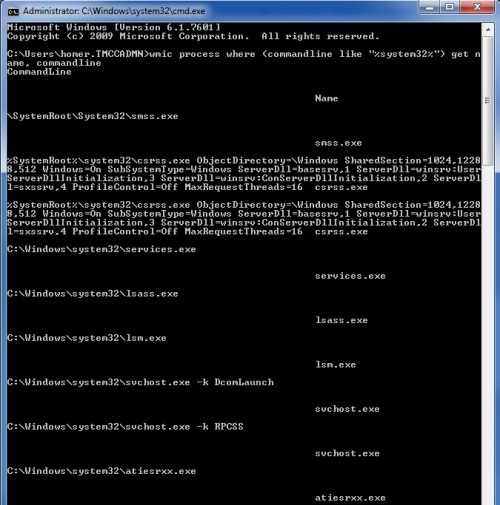
you should have some apps running from system 32 this is how I first tested it so I saw results
from a command window type
WMIC PROCESS where (commandline like "%system32%") get name, commandline
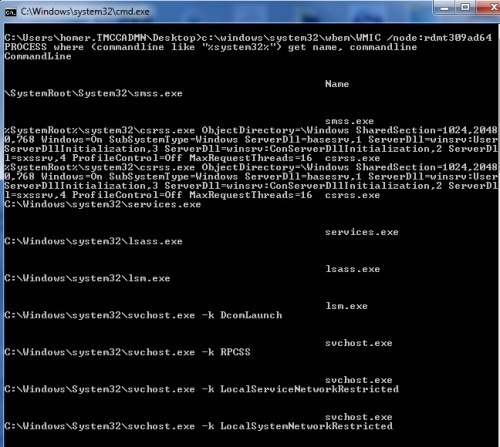
from a batch file I used: (the /node: is to query a remote machine)
c:\windows\system32\wbem\WMIC /node:rdmt309ad64 PROCESS where (commandline like "%%system32%%") get name, commandline
Comments:
-
ok i got some data in there now. Will update you in the morning, this is doable with a custom inventory rule, I just want to get a sample of data to see how the report will actually look - Scott Smith 11 years ago
-
great thanks Scott, have an action created used the batch file verbage and changed my variable from %%system32%% to %%temp%% and I see a couple of machines populating the software item. Look forward to see the report layout. When you get done you need to post this as a blog also
ShellCommandTextReturn(c:\windows\system32\wbem\WMIC PROCESS where (commandline like "%%temp%%") get name, commandline) - SMal.tmcc 11 years ago


